Digital transformation has reshaped how businesses operate, and with it, the concept of identity has evolved. No longer limited to human users, today’s enterprises rely on machine identities non-human entities that authenticate, communicate, and execute critical workflows. From cloud workloads and DevOps pipelines to IoT devices and AI driven automation, machine identities now outnumber human users in many organizations.
Yet, despite their growing importance, these identities often remain unmanaged, overprivileged, and vulnerable making them prime targets for cyberattacks.
What Are Machine Identities?
Machine identities are digital credentials that enable secure authentication and communication for non-human entities. These include:
Unlike human users, machine identities operate silently in the background often with persistent access, excessive privileges, and weak rotation policies. This makes them a goldmine for attackers looking to escalate privileges or move laterally across networks.
Why Machine Identity Governance is Critical Neglecting machine identities leads to security blind spots and compliance risks. High profile breaches often stem from exposed API keys, misconfigured service accounts, or hardcoded credentials. In cloud native environments, where workloads scale dynamically, the risks multiply.
Key challenges include:
Credential sprawl – Uncontrolled accumulation of machine identities with no clear ownership
Privilege creep – Over permissioned service accounts increasing attack surfaces
Manual mismanagement – Secrets stored in plaintext, hardcoded scripts, or shared carelessly
Audit gaps – No visibility into who created an identity, what it accesses, or if it’s still needed
Security teams can’t protect what they can’t see. Without governance, machine identities become invisible and exploitable.
The Expanding Attack Surface
Machine identities now permeate every layer of IT:
Attackers exploit these weak points through credential harvesting, token theft, and privilege escalation. Worse, breaches often go undetected for months because machine activity isn’t logged or monitored effectively.
How to Secure Machine Identities: A Lifecycle Approach
To mitigate risks, organizations must adopt automated, policy driven governance for non-human identities. Here’s how:
1. Discovery & Inventory
Scan systems, code, and cloud environments to detect unmanaged credentials.
2. Classification & Ownership
Tag identities by criticality and assign ownership to ensure accountability.
3. Least Privilege Access
Enforce role based policies grant only necessary permissions.
4. Automated Secret Management
Encrypt & rotate credentials eliminate hardcoded secrets.
5. Continuous Monitoring
Log machine activity and detect anomalies (e.g., unusual API calls).
6. Timely Decommissioning
Remove orphaned identities when systems retire.
The Future: Trust in Automation
As AI, RPA, and autonomous systems grow, so will the complexity of machine identities. Organizations must ensure:
Why Partner with Bridgesoft?
Our identity centric security solutions are designed for modern enterprises, providing:
Machine identities are the backbone of automation secure them with Bridgesoft.
In recent years, the strategic role of Identity and Access Management (IAM) has undergone a dramatic transformation. Once viewed primarily as a back-office function confined to IT departments, identity is now central to the success of digital business initiatives, cybersecurity strategies, and regulatory compliance efforts.
This evolution has been driven by a convergence of forces: the shift to cloud-based infrastructure, the rise of hybrid work, the increasing complexity of access environments, and the growing sophistication of cyber threats. As organizations expand their digital footprint, the challenge of managing who has access to what and ensuring that access is appropriate, secure, and accountable has never been more urgent.
Identity has become the control plane for modern enterprises. It is the common thread connecting employees, contractors, third-party partners, and machine identities to the systems and data they need. And because every interaction starts with identity, it is now a primary target for adversaries. Compromised credentials are consistently cited as a leading cause of breaches across industries.
Organizations are no longer operating within traditional network perimeters. The rapid adoption of SaaS applications, remote work environments, and third-party integrations has pushed access outside the enterprise boundary. As a result, identity is now the last line of defence. Effective identity governance enables real-time visibility and control over access, mitigating the risk of lateral movement in the event of a breach and limiting exposure to sensitive data.
Modern identity programs go far beyond provisioning accounts and managing passwords. When aligned with broader business objectives, IAM can accelerate user onboarding, streamline compliance reporting, reduce operational overhead, and improve the user experience.
For example, by integrating identity systems with HR platforms, access can be automatically assigned and revoked as users join, move, or leave the organization. This reduces manual effort and human error, while ensuring users have the right access at the right time. Additionally, advanced capabilities like identity analytics and AI-powered anomaly detection enable security teams to proactively respond to access-related risks helping to shift identity from a reactive function to a strategic advantage.
A successful identity program requires coordination across multiple stakeholders security teams, IT operations, HR, compliance, and business unit leaders. Yet in many organizations, these functions operate in silos. IAM implementations often stall due to unclear ownership, conflicting priorities, or poor communication between departments.
Establishing a cross-functional identity governance model can help bridge these gaps. This means bringing stakeholders together to define common objectives, clarify roles and responsibilities, and establish metrics that align with broader business goals. With the right collaboration, IAM can become a unifying force rather than a point of friction enabling secure
As digital ecosystems grow more complex and interconnected, identity will continue to play a defining role in shaping enterprise risk and opportunity. Organizations that recognize IAM as a strategic asset and invest in building mature, outcome-driven identity programs will be better positioned to thrive in a fast-changing landscape.
Ignoring identity’s expanding role comes at a cost. Whether it’s through compliance gaps, delayed onboarding, or increased exposure to threats, treating IAM as a low-priority technical project is a missed opportunity. The organizations that succeed will be those that elevate identity to the level of strategic infrastructure on par with cloud, data, and cybersecurity.
Partner with Bridgesoft to Transform Identity into Opportunity
At Bridgesoft, we understand that identity is more than just a technical control, it's the foundation of trust, security, and agility in today’s digital enterprise. With deep expertise in IAM strategy, deployment, and governance across industries, we help organizations turn identity challenges into business enablers. Whether you’re modernizing your access architecture, achieving compliance, or preparing for the next phase of digital growth, Bridgesoft delivers customized, scalable solutions to meet your unique needs.
We've all been there, right? That frustrating dance between getting our work done and navigating the labyrinth of cybersecurity. Organizations are rightly strengthening their digital defenses, but it often feels like every new security measure another authentication step, an extra access form, a policy update – adds friction. While these steps are designed to boost security, they can also leave us feeling frustrated and slow down our productivity.
But here's the thing: this trade-off is no longer acceptable. In today's hyper-digital world, how we interact online defines everything, from customer engagement to employee productivity. That means user experience isn't just a nice-to-have; it's a fundamental security requirement. For identity and security leaders, finding that sweet spot between robust protection and effortless usability has become one of the most pressing challenges.
Security That Empowers, Not Impedes
Think about it: when security controls become a roadblock to getting work done, what happens? People find workarounds. They might reuse passwords, share credentials, or even squirrel away sensitive information in less-than-secure spots. These aren't acts of negligence; they're often cries for help, signals that our security strategy isn't quite in sync with how people operate.
This is where modern Identity and Access Management (IAM) solutions truly shine. They're evolving to match the pace and reality of how we work. Imagine adaptive authentication that understands your context, single sign-on (SSO) that eliminates repetitive logins, or even a future where passwords are a thing of the past. These aren't just buzzwords; they're practical ways to enhance security without forcing users to jump through unnecessary hoops. When security feels seamless, people embrace it, and in turn, risk naturally decreases.
Weaving Design Thinking into Identity Programs
User-centric design isn't just for marketing and product teams anymore; it's a powerful tool for identity strategy. By embracing principles like empathy, rapid prototyping, and continuous iteration, identity leaders can craft workflows and access controls that genuinely reflect user needs.
Take, for instance, designing a new role-based access request system. Instead of simply building it and expecting people to adapt, imagine starting with conversations across different business units. What do users really need access to? How often do those needs shift? And crucially, by building in feedback loops, identity teams can constantly refine these systems based on real-world usage. The outcome? A more intuitive experience for users and a more efficient system for IT and security teams to manage. It's a win-win.
Building Trust Through Openness
Security shouldn't feel like something imposed on users; it should be something they understand and trust. When people are informed about why certain controls are in place, and when they have clear, easy-to-navigate options for requesting access or reporting issues, they're far more likely to embrace and adhere to security protocols.
Providing self-service capabilities, transparent access policies, and real-time visibility into permissions cultivates a culture of trust across the organization. It transforms security from a stern gatekeeper into a collaborative partner one that empowers employees to work confidently, knowing they're protected.
The Bridgesoft Perspective: Security as an Enabler
Ultimately, the most successful identity programs are those built with people at their core. When user experience and security are viewed as complementary forces rather than opposing ones, organizations can create digital environments that are both robustly secure and truly supportive.
At Bridgesoft, we believe that IAM shouldn't force anyone to choose between security and speed. With the right tools, the right mindset, and the right processes, it's not only possible to deliver both, but to elevate the identity function into a genuine driver of business value. We empower organizations to build secure, seamless digital experiences that foster productivity and trust, because we understand that the human element is at the heart of every successful cybersecurity strategy.
Identity is no longer a background function. It’s a strategic driver of security, user experience, digital transformation, and even competitive advantage. As cloud adoption, remote work, and regulatory demands reshape the enterprise, identity has emerged as the control plane for the modern organization.
But this landscape is far from static. The next evolution of identity is already underway, shaped by emerging technologies, evolving threats, and rising expectations from users and regulators alike.
Understanding what’s next is essential for IAM leaders, CISOs, and IT decision-makers looking to future-proof their programs. This post explores the key trends that will define the future of identity and what organizations can do now to prepare.
Traditional identity models rely on centralized providers directories, identity platforms, or federated systems to verify and store credentials. But with increasing concerns about data privacy, portability, and control, decentralized identity (DID) is gaining traction.
In a decentralized identity ecosystem, individuals manage their own credentials using digital wallets. Verifiable credentials such as proof of employment, age, or certifications are issued by trusted authorities and presented only when needed. No centralized store, no password reuse, and no unnecessary collection of PII.
This model holds enormous promise:
However, adoption will take time. Standards like W3C’s DID and Verifiable Credentials are still maturing, and interoperability challenges remain. But make no mistake: user-centric identity is coming, and it will shift how organizations think about onboarding, access, and trust.
Artificial Intelligence is rapidly transforming cybersecurity and identity is no exception. On one side, IAM platforms are integrating AI to drive efficiency and enhance risk detection. On the other, identity systems are becoming core data sources for AI models.
AI-powered IAM brings benefits such as:
But there’s also a growing recognition that identity data itself is a critical input to AI governance. As enterprises deploy AI models, identity will help answer questions like: Who trained this model? Who can modify it? Who is responsible for its outputs?
Going forward, expect to see tighter integration between identity governance and AI governance especially in regulated industries where explainability and accountability are key.
Passwords have long been the weakest link in security. They’re reused, forgotten, phished, and frequently compromised. Organizations have responded with MFA, but even that’s not immune to sophisticated attacks like MFA fatigue and phishing kits that intercept codes.
Now, a true shift is underway: passwordless authentication is moving from aspiration to standard.
Technologies like FIDO2/WebAuthn, biometric authentication, and device-based identity are allowing organizations to eliminate passwords altogether replacing them with cryptographic credentials stored on user devices.
This improves:
Adoption is growing, especially in customer-facing apps and modern workforce platforms. Within the next few years, passwordless will likely become the norm and organizations still reliant on passwords will find themselves increasingly exposed.
As discussed in earlier posts, non-human identities including APIs, service accounts, bots, and containers now outnumber human users in many environments. Yet governance for these identities is still catching up.
In the future, expect to see:
Organizations that delay governance in this area are inviting risk. Just as we’ve matured our processes around joiners, movers, and leavers for people, we must now do the same for code.
As threat actors increasingly target identities rather than infrastructure, Identity Threat Detection and Response (ITDR) is emerging as a key pillar of modern security.
ITDR involves detecting, investigating, and responding to identity-related threats such as privilege escalation, lateral movement via service accounts, and misuse of legitimate credentials.
Expect to see:
Identity isn’t just about provisioning anymore. It’s about active defense and ITDR is how organizations will stay ahead of adversaries.
Historically, compliance was a periodic effort to prepare for the audit, run the reports, close the gaps. But as regulations evolve and expectations shift, compliance is moving toward real-time, continuous assurance.
This requires:
IAM platforms will need to evolve from systems of record to systems of accountability, capable of proving compliance on demand and adapting to new rules as they emerge.
The future of identity is not a single destination it’s a constantly evolving landscape shaped by technology, threat actors, business needs, and user expectations. As identity becomes more decentralized, intelligent, and embedded into everything we do, the organizations that thrive will be those that embrace change, invest in innovation, and treat identity as strategic infrastructure.
Identity isn’t just a pillar of cybersecurity anymore. It’s the backbone of digital trust.
As cloud adoption continues to accelerate, identity has become one of the most critical and complex components of enterprise security. Organizations are no longer relying on a single cloud provider or data center; instead, they are operating in multi-cloud and hybrid environments that span public clouds, on-premises systems, SaaS platforms, and legacy infrastructure.
This fragmented landscape presents a growing challenge: how to manage identity consistently across a diverse, dynamic IT ecosystem. It’s not just about keeping users connected it’s about keeping access secure, compliant, and scalable without slowing down innovation.
Solving this challenge starts with a shift in mindset: identity must be viewed not as a one-time project, but as a foundational architecture layer one that underpins access, governance, and risk across every platform the business touches.
The move to cloud is rarely all-or-nothing. Many organizations adopt cloud services incrementally, driven by specific business needs. A company might use AWS for development, Azure for Office 365, and Google Cloud for data analytics all while retaining core legacy systems on-premises due to regulatory or operational constraints.
This flexibility comes at a cost. Each environment may have its own identity model, access controls, and integration capabilities. Without a unified strategy, this leads to identity silos: users with duplicate accounts across systems, inconsistent roles and entitlements, and gaps in visibility. These silos increase risk, reduce efficiency, and make compliance audits far more difficult.
Additionally, the growing number of non-human identities such as service accounts, bots, and machine workloads adds complexity. These identities often lack proper governance, creating blind spots and potential entry points for attackers.
Traditional IAM solutions were built for centralized environments, where users and resources were confined to a corporate domain. In today’s distributed architecture, this model breaks down. Manual provisioning, static policies, and point-to-point integrations simply cannot keep pace with the velocity and scale of modern cloud environments.
When identity is managed in silos, the business suffers:
To address these challenges, organizations must adopt a cloud-ready identity architecture one that is unified, automated, and policy-driven.
Building an identity strategy that spans cloud and on-premises systems requires several key capabilities:
A strong, cloud-ready identity strategy is key to secure, compliant, and scalable operations.
See how Bridgesoft can unify and automate identity across your cloud and on-premises systems: Bridgesoft Identity Solutions
Mergers and acquisitions (M&A) are often positioned as growth catalysts — opportunities to enter new markets, acquire talent, expand offerings, or streamline operations. But while financials, legal exposure, and cultural alignment often dominate the M&A due diligence process, one critical area is frequently overlooked: identity governance.
When two organizations join forces, their IT ecosystems must be integrated, aligned, and secured — and identity is at the center of that effort. Yet in many cases, identity and access management (IAM) challenges surface only after the deal is signed, when integration is already underway. By then, it’s often too late to prevent the risks: over-provisioned accounts, orphaned access, regulatory gaps, and delayed synergies.
In today’s digital-first enterprises, failure to address identity early in the M&A process isn’t just a missed opportunity — it’s a hidden liability.
When two companies merge, their user populations double overnight. Employees, contractors, partners, and systems must quickly gain access to shared resources — from collaboration tools and business applications to customer data and internal systems. At the same time, access must be governed carefully to prevent security breaches, conflicts of interest, or compliance violations.
This rapid scaling of access often introduces chaos:
Legacy identity systems with conflicting architectures
These challenges become particularly acute when the organizations involved operate in regulated industries such as finance, healthcare, or energy, where identity governance is tightly tied to compliance mandates.
Without proper identity governance, M&A activities can introduce multiple categories of risk:
Identity governance must become a formal component of M&A due diligence. This means evaluating the maturity, architecture, and risk posture of each entity’s IAM program before integration begins. Key questions to ask include:
By answering these questions upfront, organizations can identify integration gaps, anticipate challenges, and begin to define a roadmap that aligns with both security and business goals.
There is no one-size-fits-all approach to identity integration during M&A. The right strategy depends on the size, complexity, and timelines involved. However, the most effective approaches share three key characteristics: visibility, unification, and governance.
Here are four common strategies:
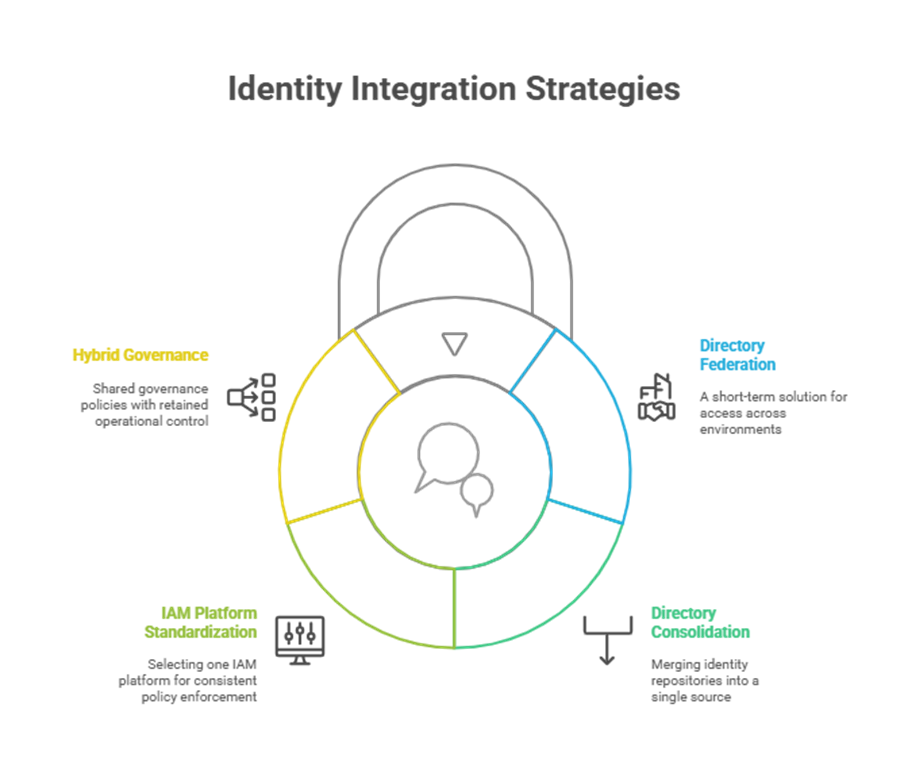
Regardless of the model chosen, the integration must be governed by clear policies, documented processes, and continuous monitoring.
Even with a solid strategy in place, the post-merger period brings unique identity risks that must be proactively managed:
IAM leaders should create a post-merger identity scorecard that tracks key metrics — such as number of identities reconciled, accounts decommissioned, and policy violations resolved — to guide integration efforts and report progress to leadership.
Rather than being a drag on M&A execution, IAM can be a powerful accelerator — if approached strategically. Mature identity governance accelerates onboarding, simplifies audit preparation, and increases organizational agility during a time of high change.
Imagine being able to grant access to new systems in hours rather than weeks. Or having a unified view of all user entitlements across both organizations. Or being able to assure the board and regulators that access to sensitive systems is fully under control.
This is the promise of treating identity not just as a technical function, but as a core M&A capability.
Don’t Let Identity Chaos Undermine Your M&A Success
A well-planned IAM strategy doesn’t just prevent disasters—it accelerates integration, ensures compliance, and protects your investment.
Ready to secure your merger with a proven identity governance strategy?
Visit Bridgesoft today to learn how we help enterprises turn IAM from a risk into a competitive advantage.
For years, cybersecurity programs were anchored in infrastructure: firewalls, antivirus software, and perimeter defense. Identity and Access Management (IAM) was often seen as an operational function important, but isolated from the broader conversation around enterprise risk.
Today, that model no longer holds.
In a digital first, cloud driven world, identity has become the new security perimeter. It defines who (or what) has access to sensitive systems, data, and workflows. And because every breach, escalation, or misconfiguration ultimately traces back to a question of identity, a modern security culture must begin with identity at its core.
But culture isn’t a product you can deploy. It’s a mindset. It requires buy in from stakeholders, clarity in roles, and sustained reinforcement across the organization. Building an identity first security culture means embedding identity into every layer of business operations and making it everyone’s responsibility.
As hybrid work, cloud adoption, and API driven development reshape enterprise environments, traditional network perimeters have eroded. Users, applications, and workloads now connect from anywhere across unmanaged devices, third party networks, and distributed systems.
In this model, the question is no longer “Is this network secure?” but rather “Should this identity have access right now?”
Security outcomes increasingly depend on identity decisions:
An identity first approach shifts the focus from controlling access at the edge to governing access at the source based on who the user is, what they need, and how their risk posture changes over time.
Adopting an identity first culture involves more than new tools or policies. It requires changing how people think, behave, and prioritize.
1. From IT Ownership to Shared Accountability
IAM has traditionally been owned by IT, but identity is now a shared responsibility. HR provides attributes. Security defines policies. Business managers approve access. Compliance teams ensure oversight. Identity affects and is affected by every function. Success depends on alignment and accountability across stakeholders.
2. From Reactive Compliance to Proactive Governance
Rather than scrambling to fix access before audits, identity first organizations bake governance into everyday workflows. Role definitions are clear. Entitlement reviews are automated. Violations are detected in real time. Identity controls become part of the organization’s operating system.
3. From Static Permissions to Dynamic Access
In fast moving environments, static access grants quickly become outdated. Identity first thinking embraces principles like least privilege, just in time (JIT) access, and contextual authentication. It treats access as a temporary condition not a permanent entitlement.
1. Executive Sponsorship
Without leadership support, identity programs often stall due to lack of prioritization or funding. Executives must champion identity as a business enabler, not just a security requirement. Metrics tied to business value such as time to productivity, risk reduction, or audit readiness help build support across the C suite.
2. Identity Literacy Across Teams
Just as cybersecurity awareness training is standard practice, identity awareness should be part of organizational onboarding and training. Managers need to understand their role in access approvals. Developers need to know how to secure service accounts. Employees must recognize their role in protecting credentials and reporting suspicious access.
3. Seamless User Experience
Security that disrupts users is often bypassed. Identity first organizations prioritize security by design making secure behavior the path of least resistance. This includes intuitive access requests, SSO, passwordless authentication, and clear visibility into who has access to what and why.
4. Continuous Improvement
Identity governance is not a “set it and forget it” effort. Business roles change. Technologies evolve. Threats adapt. A culture of continuous improvement with regular policy reviews, feedback loops, and automation audits ensures that identity programs remain relevant and effective.
If your organization is looking to build or reinforce an identity first culture, start with the following foundational steps:
While culture is people first, technology plays an enabling role. Identity first cultures benefit from platforms that:
Technology should not be the culture but it should make the culture easier to adopt, enforce, and evolve.
Culture is the force multiplier of security. Policies can be written. Tools can be deployed. But without a culture that values identity as a strategic asset, even the most advanced IAM implementations will fall short.
An identity first culture ensures that access is governed by design not by default. It empowers people to make informed decisions, respond to risk quickly, and align access with the needs of the business.
In a world where identity is both the new perimeter and the new attack vector, culture isn’t just a nice to have. It’s your strongest line of defense.
Identity and Access Management (IAM) is the backbone of enterprise security, ensuring the right people have the right access at the right time. But too often, IAM teams struggle to prove their value beyond basic compliance checkboxes.
If you're still measuring success by the number of roles created or users onboarded, you're missing the bigger picture. Real IAM success isn’t about system outputs; it’s about business outcomes.
Why Most IAM Metrics Miss the Mark

These metrics might look good on a dashboard, but they don’t answer the critical questions executives care about:
✔ Are we reducing risk?
✔ Are we improving efficiency?
✔ Are we enabling the business?
Without meaningful metrics, IAM teams get stuck in a cycle of "keeping the lights on" instead of driving strategic value.
The 3-Tier Framework for IAM Metrics That Matter
To shift from tactical reporting to business-aligned measurement, focus on three key areas:
1. Operational Metrics: Is IAM Running Smoothly?
These track efficiency and system health:
Example: A company reduced access provisioning from 5 days to 2 hours by automating workflows cutting onboarding costs by 30%.
2. Risk & Compliance Metrics: Are We Actually Safer?
These prove security effectiveness:
Example: After implementing just-in-time access, one firm reduced standing privileged accounts by 75% dramatically shrinking their attack surface.
3. Business Impact Metrics: Does IAM Drive Value?
These connect identity to strategic goals:
Example: A retailer’s streamlined customer IAM (CIAM) platform boosted checkout completion by 15% adding millions in revenue.
Turning Data into Decisions
Tracking metrics is useless unless they drive action. Here’s how to operationalize them:
IAM isn’t just about security it’s a business accelerator. The right metrics will help you:
"What gets measured gets improved." Start measuring what matters.
Ready to elevate your IAM metrics? Contact us today and let’s turn identity into your competitive advantage.
Imagine your phone, computer, or favorite app being compromised, wouldn’t you want an immediate solution?
Well, lucky for you, there is one! There’s a digital detective whose job is to figure out who did it, how they did it, and what they accessed. That’s what Cyber Forensics is all about, solving digital crimes by collecting and analyzing evidence from electronic devices.
Now, here’s where IAM, short for Identity and Access Management, becomes a hero:
IAM is like the bouncer at a VIP party. It decides who gets in, what rooms they can enter, and what they’re allowed to do. And when something goes wrong, IAM keeps a record of every door opened and by whom. Think of it as having a detailed guest list and security footage at every door.
This makes Cyber Forensics faster and more accurate because investigators can trace digital footprints back to specific users or actions. Meaning that we are able to let you rest, knowing that you’re safe.
So in today’s world of constant digital threats, IAM isn’t just about security. Let’s imagine a scenario together so that you will know what to do in a situation where Cyber Forensics is needed. Because IAM is also about catching criminals.
You have just received an email from our cybersecurity team, telling you and the team to be cautious in opening suspicious emails or answering any call that requests us to log in to the link(s) that they provide.
Everyone began to question what was happening and found that there was a threat actor (TA) attempting to impersonate an IT support personnel, asking employees to log in to a link in order to get their user ID and password, also known as a user's login credentials.
The TA can use the login of whoever falls for the trick and get confidential company information. We were all relieved to find that our identity and access management (IAM) security awareness program was able to save the company from the cyber attack.
So, what exactly happened? The TA was able to convince one employee to create a login, hence getting access to their credentials. The TA then tried to log in to our company’s application from his device, in which he was prompted to use two-factor authentication.
The user was told to give him the authentication code which raised a red flag. It is
known that people are not meant to share the code with anybody especially for something important. The user immediately hung up and reported the incident to our security team…
This is known as an outsider threat, which happens when a person outside of a secure system manages to get in and essentially steal, change or block access to data.
However, companies must also be wary of the people on the inside, individuals within the system who misuse their access. IAM systems enhance digital forensics by monitoring user access, enforce stricter controls, and strengthen security overall.
IAM and Cyber Forensics play hand in hand together, and with this example above, it’s clear it’s more common than we think.
Every time you log into your email, swipe your access card at work, or even unlock your phone with Face ID, IAM is quietly working in the background. It’s making sure you are really you, and that you’re only accessing what you’re supposed to.
But when something goes wrong, like a data breach or unauthorized access, Cyber Forensics steps in. And thanks to IAM logs and records, investigators can follow the digital breadcrumb trail. They can pinpoint who accessed what, when, from where, and even what device they used.
This partnership is crucial, especially today when cybercrimes are becoming more sophisticated. Without IAM, forensic experts would be digging through a digital haystack without a clue. But with IAM? It’s like turning on the lights in a dark room.
Together, IAM and Cyber Forensics don’t just help respond to attacks, they help prevent them, by tightening access controls and spotting unusual behavior before it becomes a bigger problem.
So the next time you log in somewhere or get asked to verify your identity, remember: that tiny inconvenience is actually part of a much bigger system working to keep you, and your data safe.
In today’s digital landscape, safeguarding sensitive data and ensuring regulatory compliance are top priorities for organizations. Identity Access Management (IAM) serves as a cornerstone for achieving these goals by controlling user access to critical systems and resources.
Below are key best practices to optimize your IAM strategy.
1. Develop Comprehensive IAM Policies Aligned with Business Needs
Start by defining clear IAM policies that reflect your organization’s unique requirements. This includes mapping user roles and access levels to ensure employees only have permissions necessary for their responsibilities. Implementing Role-Based Access Control (RBAC) simplifies permission management by assigning access based on job functions. Regularly revisit these policies to align with evolving business needs, ensuring scalability and agility in dynamic environments.
2. Strengthen Authentication and Access Controls
Enforce strong passwords and multi-factor authentication (MFA) to add security layers. Utilize advanced verification methods, such as biometrics or hardware tokens, to reduce unauthorized access risks. By combining security layers like encryption and least-privilege principles, organizations can create a robust defense against breaches.
3. Conduct Regular Risk Assessments and Policy Reviews
Proactively identify vulnerabilities through frequent risk assessments. This enables organizations to adjust policies and address gaps before they escalate. Schedule policy updates to stay compliant with industry regulations and adapt to emerging threats. A dynamic approach ensures your IAM framework remains resilient.
4. Automate User Lifecycle Management and Monitoring
Automate user provisioning and deprovisioning to eliminate manual errors and ensure timely access adjustments during onboarding or role changes. Implement log monitoring and automated alerts to track suspicious activities in real time. Tools that monitor access logs enhance visibility, enabling swift responses to potential incidents.

5. Integrate IAM with Security Solutions and Provide Training
Maximize protection by integrating IAM with security solutions like SIEM (Security Information and Event Management) systems. This fosters cohesive incident response strategies and centralized threat detection. Additionally, provide user training to educate employees on phishing recognition and secure access practices. An informed workforce is your first line of defense.
Why Bridgesoft?
At Bridgesoft, we understand that effective IAM requires a blend of cutting-edge technology and strategic planning. Our solutions support RBAC implementation, automated user management, and seamless SIEM integration, empowering organizations to enforce granular access controls while reducing administrative overhead.
Conclusion
Implementing these IAM best practices not only fortifies security but also enhances operational efficiency. By prioritizing policy reviews, strong authentication, and user training, businesses can build a future-proof IAM framework. Partner with Bridgesoft to leverage tailored IAM strategies that align with your organizational goals, ensuring secure and scalable access management.
By adopting these practices, organizations can transform their IAM approach into a strategic asset, driving both security and productivity.
In today's ever-evolving digital landscape, managing user identities has become increasingly complex. Businesses juggle a vast network of applications, cloud resources, and interconnected systems, each requiring secure access control. This is where Identity Governance and Administration (IGA) comes into play.
Bridgesoft, a leading provider of IGA solutions, empowers organizations to streamline identity management and bolster security. But before diving into Bridgesoft's offerings, let's delve deeper into the world of IGA and explore its significance.
Key Components of Identity Governance
An effective IGA program should include the following components:
Bridgesoft offers a robust IGA platform that caters to the diverse needs of modern organizations. Here's a glimpse into Bridgesoft's IGA solutions:
By implementing Bridgesoft's IGA solutions, you can:
If you are looking for a partner to help you implement an Identity Governance program, Bridgesoft is the perfect choice. Contact us today to learn more about our solutions.
The gaming industry is a colossal entertainment force, with millions worldwide enthralled by online games. This phenomenal growth, however, brings a rising tide of online security threats. Hackers constantly seek ways to exploit vulnerabilities in games and platforms, making robust security measures crucial for game developers and publishers to safeguard their players.
One of the most concerning issues is identity theft. Hackers can steal player accounts, wreaking havoc by cheating, pilfering in-game items, or even making real-world purchases. This can be devastating for players, potentially leading to lost accounts or compromised financial information.
Another major threat is denial-of-service (DoS) attacks. These bombard game servers with traffic, rendering them inaccessible to legitimate players. DoS attacks disrupt gameplay and cause frustration, potentially damaging a game's reputation.
Here's a glimpse into the industry's scale to emphasize the importance of security:

Bridgesoft, a company specializing in identity and access management (IAM) services, offers solutions specifically designed for the gaming industry. IAM solutions address online security challenges by providing features like:

By implementing IAM solutions, game developers and publishers can create a safer and more secure environment for their players. This safeguards them from identity theft, DoS attacks, and other online security threats.
There's more to the benefits of IAM solutions. They can also enhance the player experience by:
If you're a game publisher, prioritizing IAM solutions is vital to protecting your players and your business. Bridgesoft provides a variety of solutions to cater to your specific requirements. For more info on the gaming do check this.
To learn more about how Bridgesoft's IAM solutions can help you secure your game, visit our website or contact us directly.
In today's dynamic business environment, efficient Identity and Access Management (IAM) is critical for both security and operational success. By streamlining user lifecycle management, automating tasks, and enforcing least privilege principles, organizations can minimize risk, improve productivity, and gain a competitive advantage.
Automating user provisioning, de-provisioning, and access certifications reduces manual effort and minimizes human error. This streamlined approach enhances security and improves overall efficiency by eliminating unnecessary access requests and approvals.
Robust analytics and reporting capabilities provide valuable insights into user behavior and potential security threats. This data-driven approach enables informed decision-making, continuous process optimization, and a strong return on investment for your IAM strategy.
Five Real-World Examples of How IAM KPIs Improve Efficiency:
1. Reduced Time to Onboard New Employees:
2. Enhanced Security and Reduced Risk:
3. Improved User Experience:
4. Optimized Resource Allocation:
5. Accelerated Business Decision-Making:
The digital age demands a flawless Identity and Access Management (IAM) strategy. Businesses today rely on Okta, a leading IAM solution, to safeguard access and data across their ecosystem. But for maximum impact, Okta needs a bridge to connect it seamlessly with your existing workflows and applications. That's where Bridgesoft steps in.
We are integration specialists, and our expertise lies in bridging the gap between Okta and your business-critical systems. This powerful combination unlocks a future-proof IAM strategy that not only bolsters security but also streamlines operations and user experience.
Trending Topics in IAM: Charting the Course for Success
The IAM landscape is constantly evolving. Here are some of the hottest trends to consider when crafting your IAM roadmap:
The Bridgesoft + Okta Advantage: A Symbiotic Security Solution
By integrating Bridgesoft with Okta, you unlock a future-proof IAM strategy that delivers:
Bridge the Gap to a Secure Future
At Bridgesoft, we understand the critical role of a robust IAM strategy. Our integration experts can bridge the gap between your existing systems and Okta, empowering you to secure your digital landscape, optimize workflows, and unlock the full potential of your workforce.
Contact us today for a free consultation and discover how Bridgesoft can help you build a future-proof IAM strategy with Okta.
Ever feel bogged down by a complex Identity and Access Management (IAM) system? You're not alone. In a recent LinkedIn article by MARIA N. SCHWENGER (Link to the article), Bridgesoft tackles this common challenge head-on.
The article explores the struggles businesses face with traditional IAM solutions and how Bridgesoft's innovative approach can simplify user provisioning and access management. This can lead to significant benefits, including:
