
Mergers and acquisitions (M&A) are often positioned as growth catalysts — opportunities to enter new markets, acquire talent, expand offerings, or streamline operations. But while financials, legal exposure, and cultural alignment often dominate the M&A due diligence process, one critical area is frequently overlooked: identity governance.
When two organizations join forces, their IT ecosystems must be integrated, aligned, and secured — and identity is at the center of that effort. Yet in many cases, identity and access management (IAM) challenges surface only after the deal is signed, when integration is already underway. By then, it’s often too late to prevent the risks: over-provisioned accounts, orphaned access, regulatory gaps, and delayed synergies.
In today’s digital-first enterprises, failure to address identity early in the M&A process isn’t just a missed opportunity — it’s a hidden liability.
When two companies merge, their user populations double overnight. Employees, contractors, partners, and systems must quickly gain access to shared resources — from collaboration tools and business applications to customer data and internal systems. At the same time, access must be governed carefully to prevent security breaches, conflicts of interest, or compliance violations.
This rapid scaling of access often introduces chaos:
Legacy identity systems with conflicting architectures
These challenges become particularly acute when the organizations involved operate in regulated industries such as finance, healthcare, or energy, where identity governance is tightly tied to compliance mandates.
Without proper identity governance, M&A activities can introduce multiple categories of risk:
Identity governance must become a formal component of M&A due diligence. This means evaluating the maturity, architecture, and risk posture of each entity’s IAM program before integration begins. Key questions to ask include:
By answering these questions upfront, organizations can identify integration gaps, anticipate challenges, and begin to define a roadmap that aligns with both security and business goals.
There is no one-size-fits-all approach to identity integration during M&A. The right strategy depends on the size, complexity, and timelines involved. However, the most effective approaches share three key characteristics: visibility, unification, and governance.
Here are four common strategies:
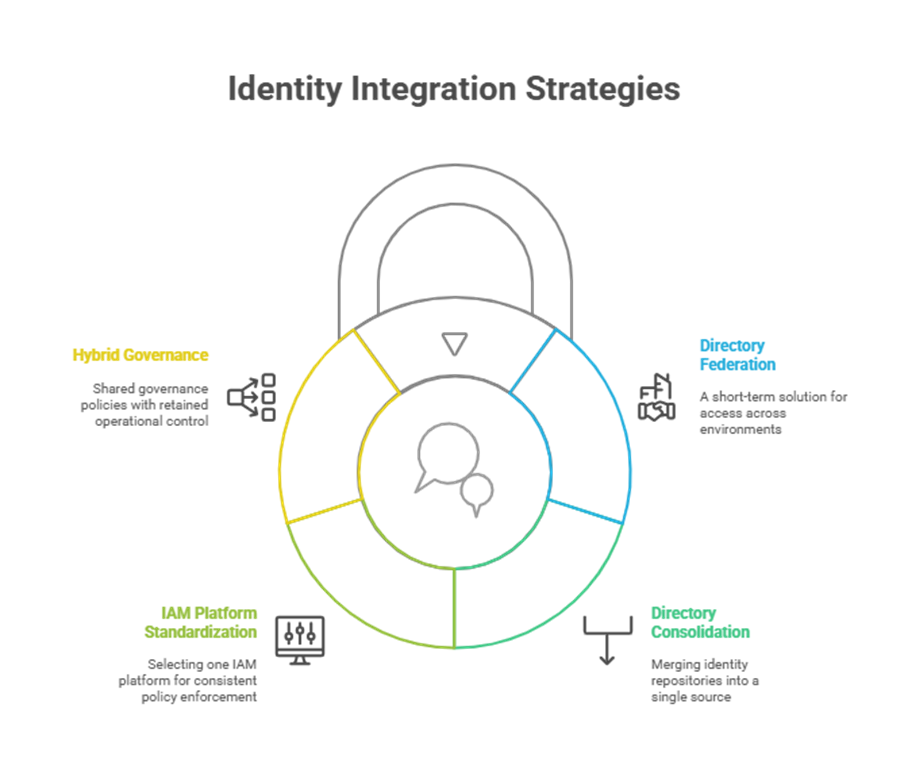
Regardless of the model chosen, the integration must be governed by clear policies, documented processes, and continuous monitoring.
Even with a solid strategy in place, the post-merger period brings unique identity risks that must be proactively managed:
IAM leaders should create a post-merger identity scorecard that tracks key metrics — such as number of identities reconciled, accounts decommissioned, and policy violations resolved — to guide integration efforts and report progress to leadership.
Rather than being a drag on M&A execution, IAM can be a powerful accelerator — if approached strategically. Mature identity governance accelerates onboarding, simplifies audit preparation, and increases organizational agility during a time of high change.
Imagine being able to grant access to new systems in hours rather than weeks. Or having a unified view of all user entitlements across both organizations. Or being able to assure the board and regulators that access to sensitive systems is fully under control.
This is the promise of treating identity not just as a technical function, but as a core M&A capability.
Don’t Let Identity Chaos Undermine Your M&A Success
A well-planned IAM strategy doesn’t just prevent disasters—it accelerates integration, ensures compliance, and protects your investment.
Ready to secure your merger with a proven identity governance strategy?
Visit Bridgesoft today to learn how we help enterprises turn IAM from a risk into a competitive advantage.
